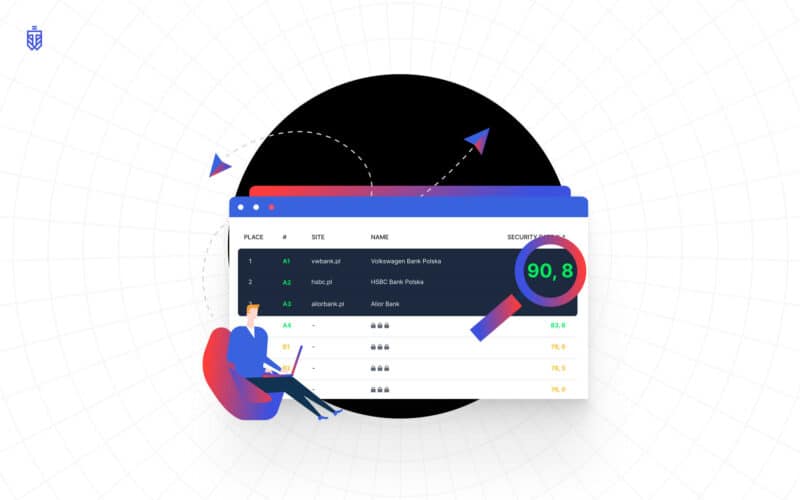
In the first half of June 2020, WebTotem researched web security issues of Polish Banks. We wanted to identify what potential attack vectors could be used by hackers. The WebTotem carried out the research using methods available to every Internet user, meaning, it did not interfere with the banking systems. Starting in October, everyone can download the report here.
The report quickly became trendy that highlights the importance of cybersecurity topics
It was featured by reputable business media such as Puls Biznesu and other trustworthy broadcasters. The report itself was downloaded from our website many times. We are glad that so many people are genuinely interested in the topic.
Yet, as it often happens with the new kid on the block, we got some kind of hate from the existing players in the local cybersecurity market. We got accused our report doesn’t add any informational value to IT security professionals, scrutinised for our particular methods of scanning, and even get objects to jokes very close to libelous statements.
Our response to the latter is that we encourage our competitors to keep it professional. As to particular methods of our research, including specific domain names, ip addresses, numbers in our methodology, we are not disclosing those details due to two reasons. First, we protect the reputation of the banks-subjects of our research. We do not distribute it out of respect to the confidentiality of their data (although, we will gladly provide every bank from our report the information about the research so it can look into the details about itself). Secondly, the specific methods of our research are our know-how, the product of our team R&D, and many years’ experience, our expertise we actively invest in. Naturally, it is also confidential.
As to accusations about how the paragraphs in the report were phrased and as if it lacks some specific examples or, on the contrary, contains information that is “non-relevant to cybersecurity”: criticizing someone is very easy, but setting an example is quite difficult.
We stand behind our statements in the report and enjoy the liberty of choosing the way of presenting the information objectively to the public
Does our report add value to IT security professionals? – it didn’t mean to do so. Our report goal is to inspire a website owner to think closely about the security of his/her website. Hackers create 300,000 new pieces of malware daily and the real cost of a hacked website extends beyond monetary value. We, at WebTotem, aim to make the Internet a safer place. And we consider raising cybersecurity awareness as an effective method to do that.
Surely, the report itself is just the tip of the iceberg of our skills and expertise in the cybersecurity area. We work hard to be the best in the field. And, we are extremely privileged to earn the TechCrunch Top Pick for Disrupt 2020, after competing with thousands of other startups from all over the world. You may read more about it here.
Was our scanning invasive? – no. We used non-invasive methods, looking into the main domain of a bank, its main page and the email server. We checked CMS and known Web components and looked for CVE, short for common vulnerabilities and exposures, guided by OWASP A9 “Using Components with Known Vulnerabilities” standard. The directory of publicly disclosed cybersecurity vulnerabilities is open for the public and we encourage the IT departments of the banks to search, use, and incorporate them into products and services. WebTotem can provide a detailed report of CVE for every bank if needed.
Why do we consider website performance parameters relevant to cybersecurity? – because it is relevant. SO/IEC 27001, the international standard on how to manage information security, indicates the availability of websites as one of the ways that help organizations make the information assets they hold more secure. Besides, the low speed of a webpage can negatively affect its reputation and might be blacklisted by Google.
Where did we get the list of headers from? – we made it by OWASP guides.
Why do we pay that much attention to the emails leaks in the banks if all bank employees must use corporate emails only? – we wish it would be so easy as it sounds! The truth is, employees use the bank’s corporate email when registering for various services. In 90% of cases, the passwords of user accounts on different services match. As a result of malicious hackers’ activity, databases of leaked emails, passwords, and other personal information appear in the network. Sometimes, in huge volumes, as in the case of LinkedIn, ProctorU, or Nintendo, 300,000 passwords of which were leaked in April 2020. Hackers can use those leaks to get access to the work correspondence of a bank employee and cause, at the minimum, reputational risks.
Which standard did we use to scan the ports and why did we scan them, in the first place? – we used OWASP standard A6 “Security Misconfiguration” do the research. We can send the list of open ports we have found to the bank of interest. While open ports are not as dangerous as they are, improperly configured server and network security rules, together with vulnerable software, can ultimately decrease network security level in the company.
How did we check GDPR compliance? – following Europe’s data privacy and security law, the overview of which one can find here.
Did we add a bit extra to our report? – yes, we included the “current state” section, whether we gathered the data from external sources about suspicious activities. Many websites do that and open data to the public.
Did we make a typo or two in our report? – yes, turns out, we did. We apologize for that.
In conclusion, we invite everyone to download our report (you can do it here). If you are an interested party and represent the bank featured in our report, we encourage you to contact us for more details. As for defamatory public post authors, we cordially offer to publish a reasonable correction of the matter in question and restrain from such unfair competition practices in the future.