- 39 secondsThere is a hacker attack every 39 seconds
- Under attack55% of SMBs have experienced a cyberattack in 2020
- Every day30 000 websites get hacked every single day
Get peace of mind with WebTotem
Stop worrying
Stop worrying about data and money loss and sleep tight, while WebTotem is doing all the work for you.
Save time and money
Save time and money on employing security specialists or trying to secure your websites on your own.
Fast setup
Forget about complicated setup, professional jargon or additional coding. Get your websites secured in 5 minutes.
All-in-One solution that protects your website
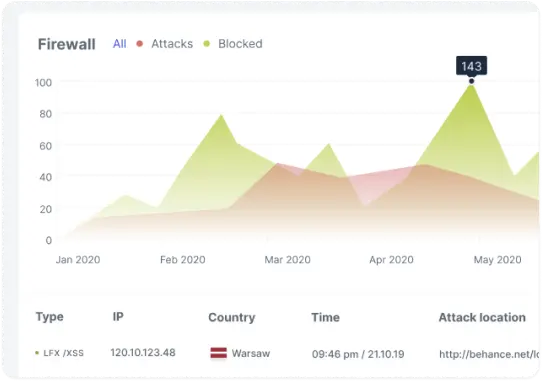
Firewall
AI-inspired proactive protection against intrusions and new emerging threats
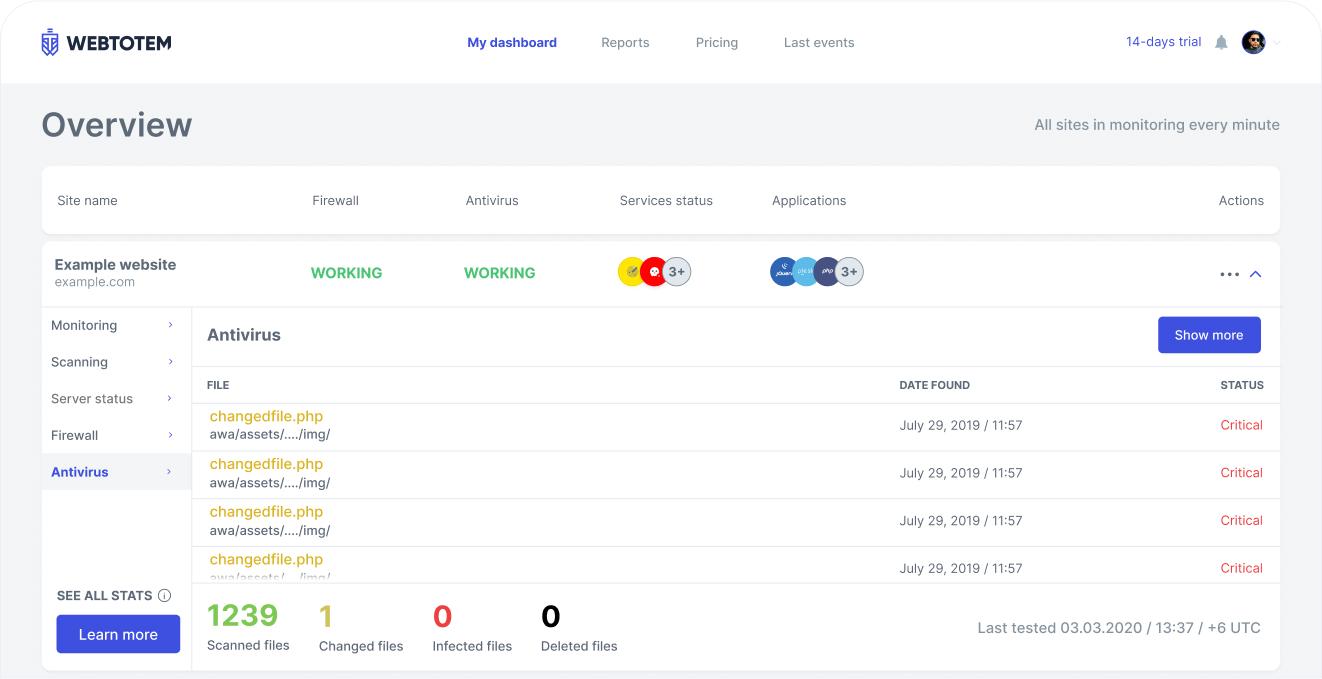
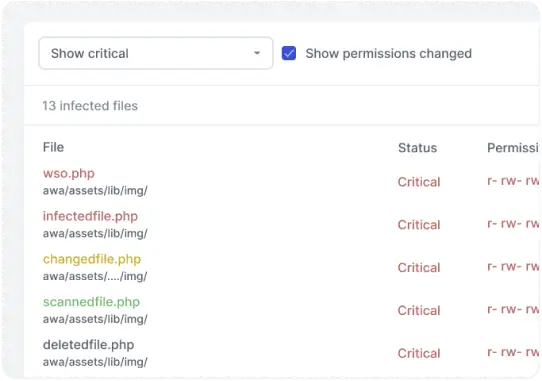
Antivirus
Server-side scanner that neutralizes malware in one click and notifies about new, modified and deleted files
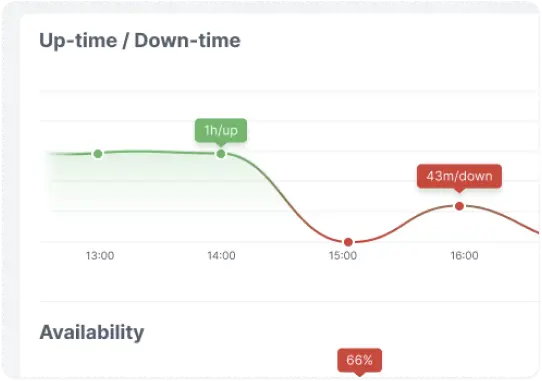
Monitoring
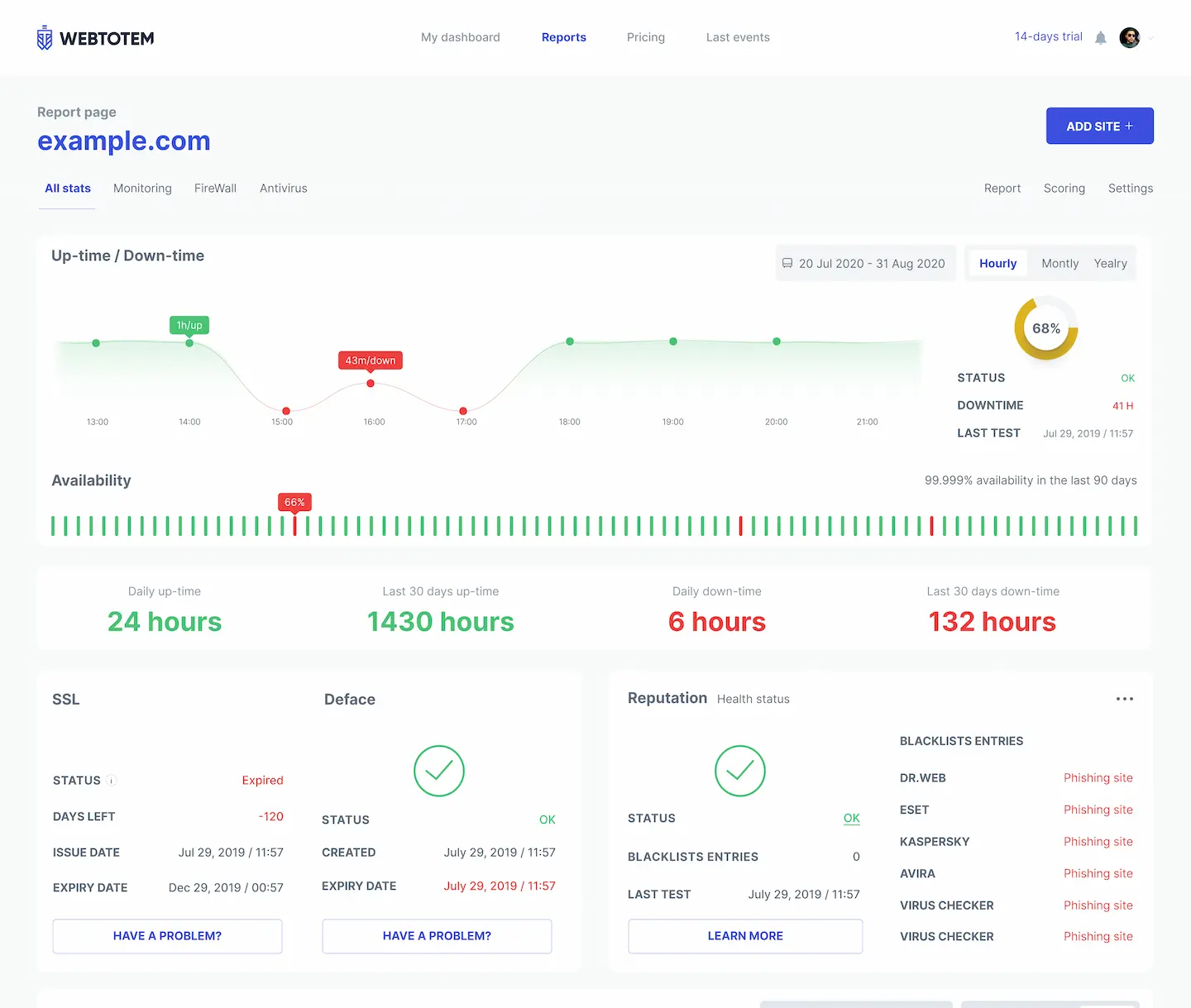
Continuous external monitoring of downtime, web reputation, SSL, domain expiry and much more
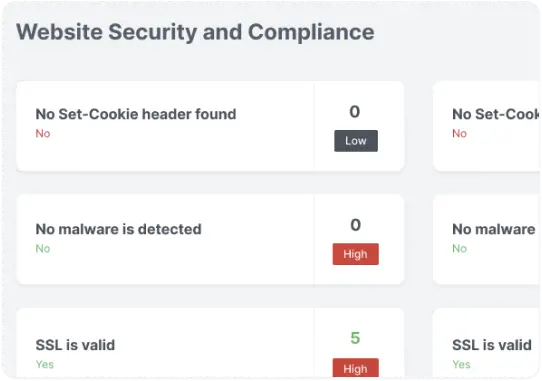
Vulnerability Management
Continuous identification and elimination of vulnerabilities
Comprehensive protection
Get notifications on security and examine the reports on the cyber threats activity
Customize the access to your websites by adding certain IPs to white/blacklists
Detect infected files and deactivate them
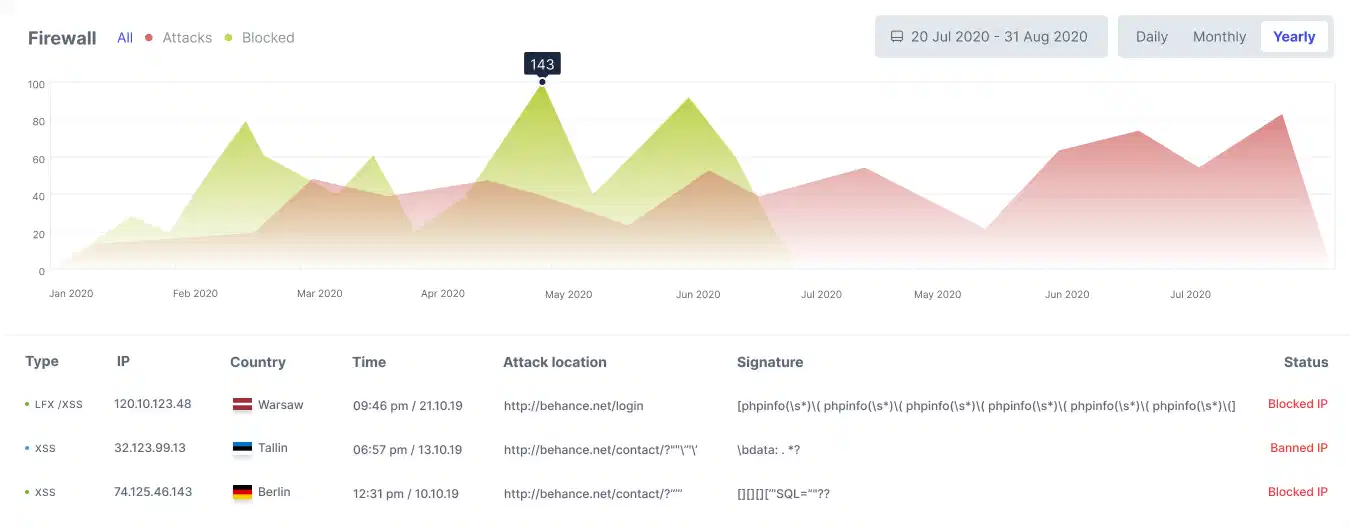
Protect websites from hackers, bad bots, SQLi, XSS, spam, Path traversal
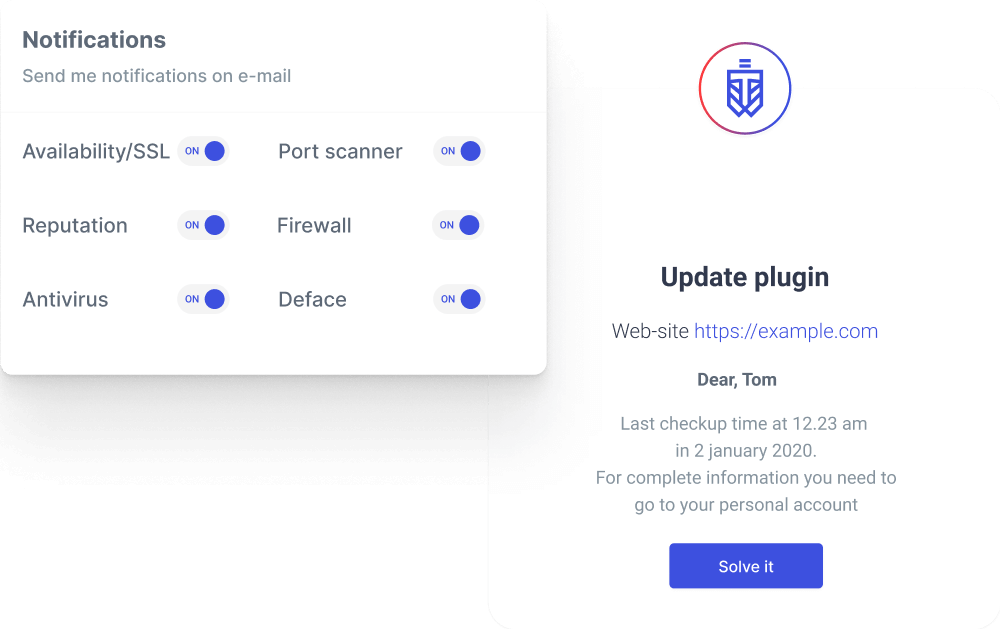
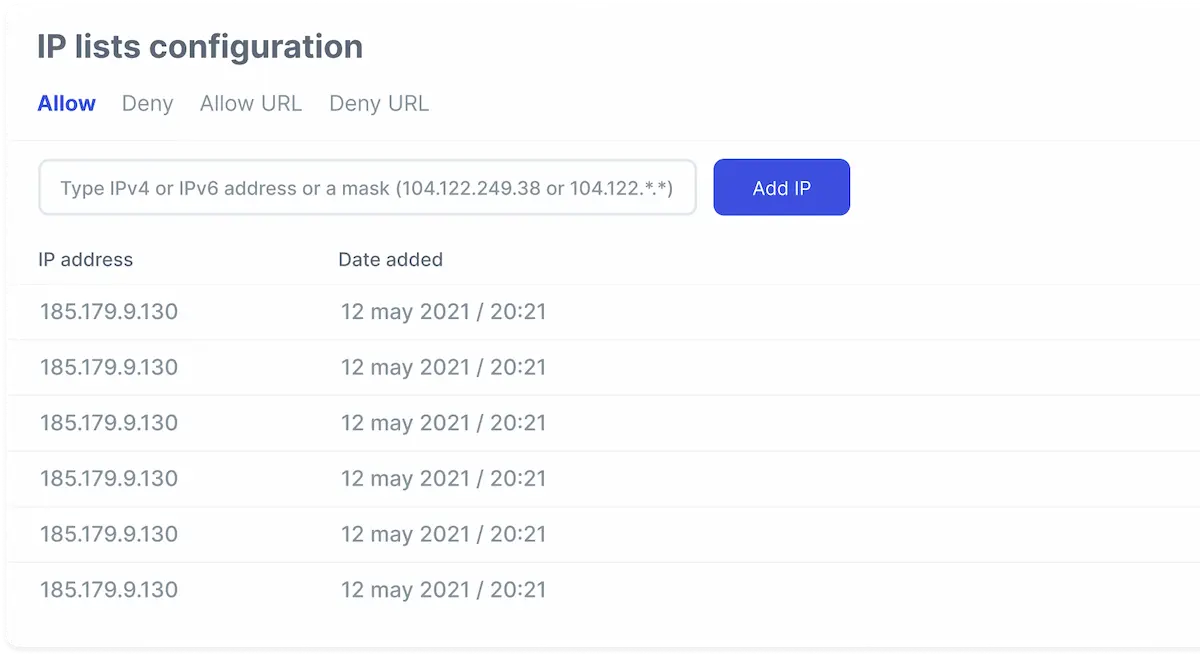
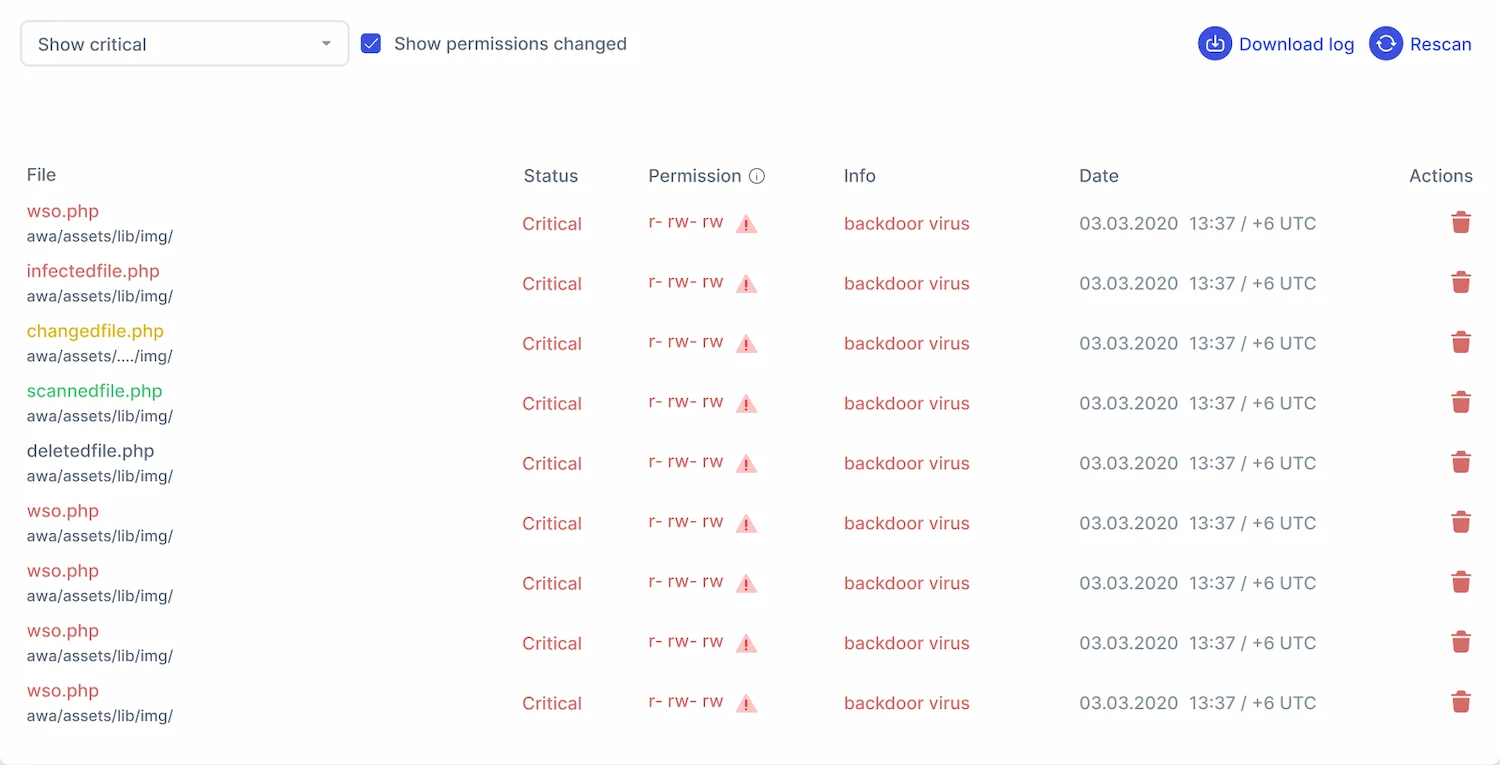
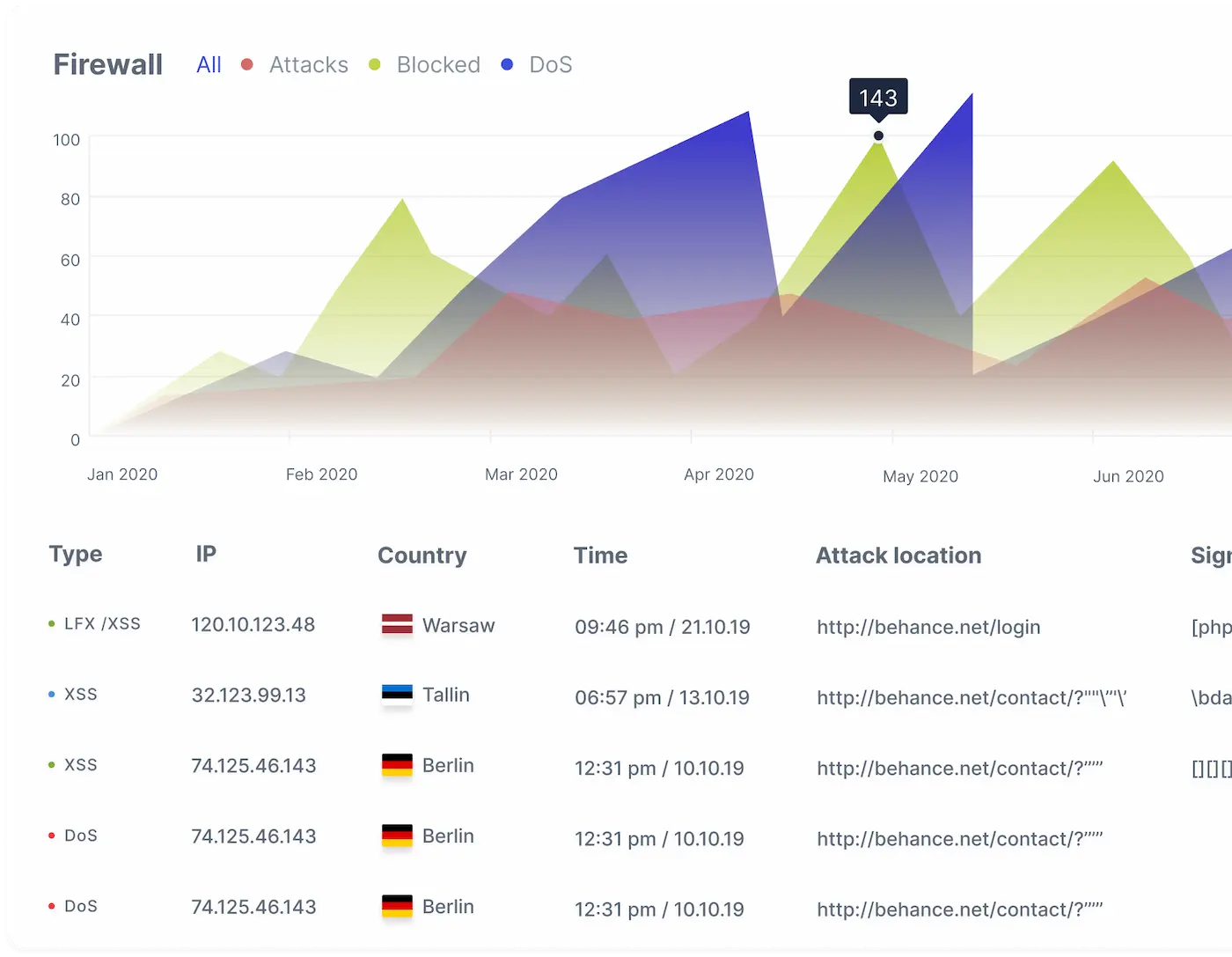
Advanced security
Collaboration
Monitor all your websites from one dashboard and find pain points at a glance
Send detailed reports on the security issues to your clients
Invite team members for collaboration

Prevent easily. Detect smartly. Respond fast.
Your personal AI-powered web application security assistant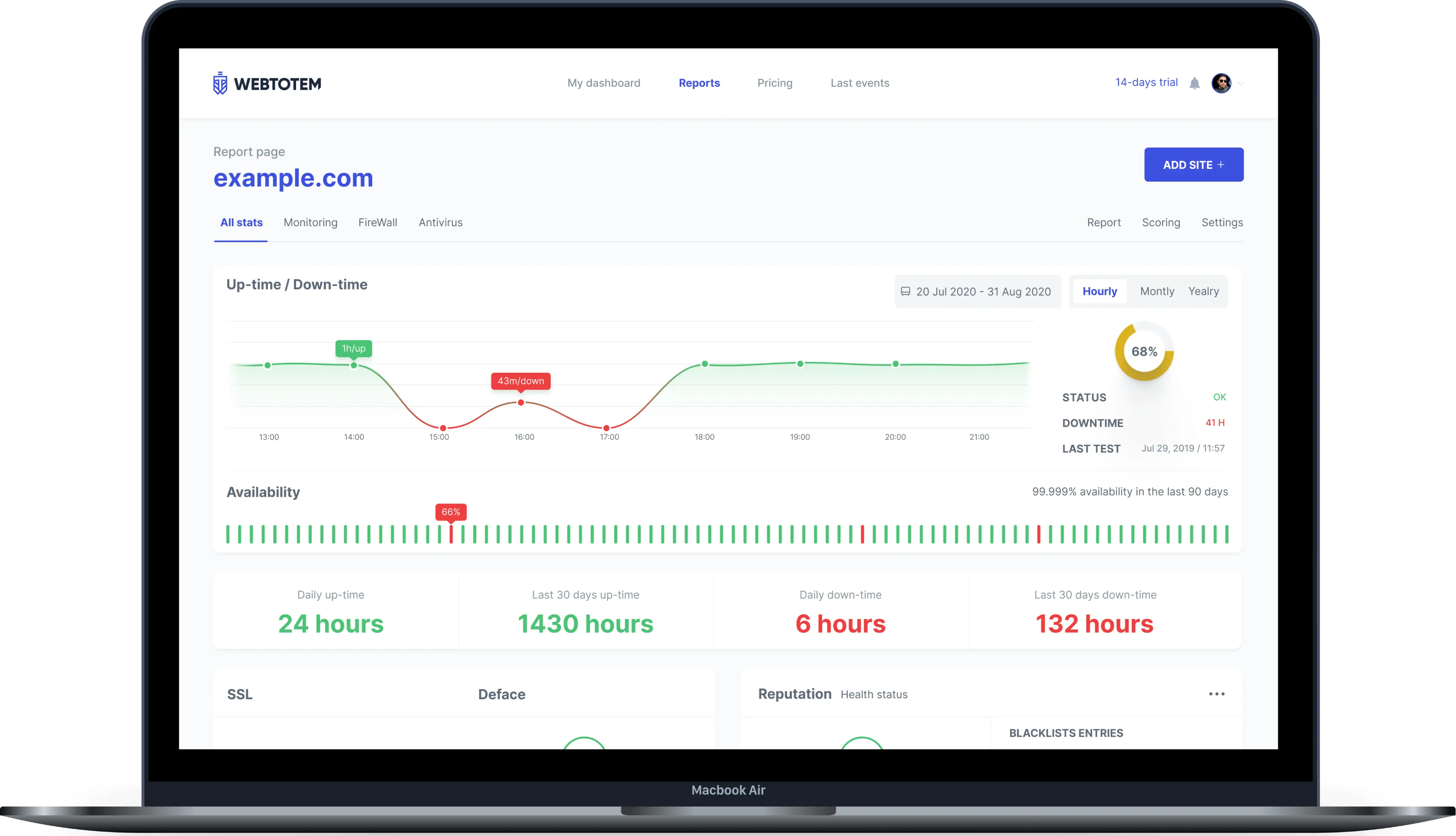
Single
The plan is perfect for a single website
$8
What's included:
- 1 Site
- Antivirus
- Web application Firewall
- SSL monitoring
- Open ports & path scanner
- Availability monitoring
- Wordpress, Plesk, Joomla, Drupal
Standard
The plan is perfect for freelancers
10$
What's included:
- 3 Site
- Everything in Single
- Website security scoring
- Blacklist monitoring
- Technology & Vulnerability scanner
- IP Reputation
- Server Resources monitoring
Professional
The plan is perfect for agencies
$18
What's included:
- Up to 50 websites
- Everything in Standard
- Central monitoringd dashboard
- Whitelabel PDF reports
- Up to 3 team members
- De-blacklisting
- High priority event support
Custom plan
If you need enterprise coverage for multiple websites, contact for a custom solution.
What's included :
Bug Bounty Plan
If security is your top priority, this plan is your ultimate solution to proactively protect your systems.
What’s included:
- All features in Professional
- Real-time dashboards
- Customizable reward tiers
- Vulnerability triage and prioritization
- Self-managed setup and management for 1 domain
- Access to 2,000+ ethical hackers / bug hunters
Get live-chat support 24/7
Need help with installation?
Having questions about the plans or features?
Contact support team 24/7 via chat or email: support@wtotem.com